A VPN passthrough is a feature on routers that allows encrypted VPN data packets from devices on your local network to pass through the router’s firewall without being blocked or dropped.
It’s important to note that VPN passthrough does not establish the VPN connection itself. The actual VPN connection is created between the device (e.g., your computer or smartphone) and the VPN server.
VPN passthrough merely facilitates the unhindered flow of this VPN traffic through your router.
Without a VPN passthrough enabled, some older VPN protocols may not work correctly due to conflicts with NAT.
Routers use NAT to allow multiple devices on a local network to share a single public IP address. The NAT type also determines how accessible your local network is from the internet.
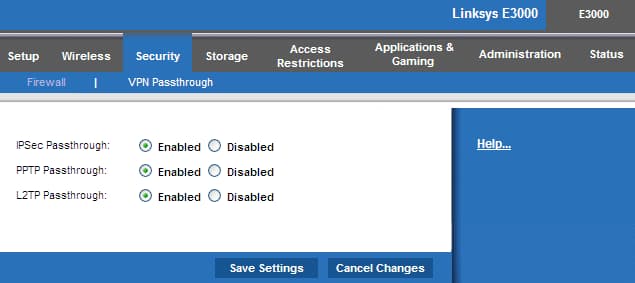
Older VPN protocols like L2TP, PPTP, and IPsec are not compatible with NAT. If you’re using a PPTP or IPsec VPN on an outbound connection without a VPN passthrough enabled, your router may drop the VPN packets or block the VPN connection altogether.
A VPN passthrough essentially forwards your VPN traffic through the router, allowing it to bypass the NAT process. For example, if you enable an IPSec passthrough, the IPsec traffic will be internally passed through to an Application Layer Gateway, which handles the redirection of traffic instead.
Newer VPN protocols like OpenVPN, IKEv2, and WireGuard are compatible with NAT, so they do not require VPN passthrough to function correctly.
By understanding how a VPN passthrough works, you can determine if enabling this feature on your router is necessary for your particular VPN setup.
How Does VPN Passthrough Work?
VPN passthrough facilitates the smooth transmission of VPN traffic through your router’s NAT process. When your VPN software attempts to connect with a remote VPN server, it uses VPN protocols to encapsulate its connection requests, which then pass through your router’s NAT.
NAT allows a single public IP address to be shared among many devices on a local network by transparently translating the private IP addresses used on the internal network into the public IP address needed for communication over the internet. It acts as an intermediary, mapping the private IP addresses to the public IP address and vice versa.
However, problems arise with older VPN protocols like PPTP, LT2P and IPsec, as these protocols encrypt and repackage data packets in a way that does not provide NAT with enough information to deliver them to their intended recipients.
There can be multiple private IPs associated with a single public address, and it’s impossible for NAT to know which one to forward the data to.
Instead of disabling NAT on your router, which is generally not advised, VPN passthrough provides a more elegant solution.
Here’s why disabling NAT is not recommended:
- IP address conservation: NAT helps reduce the need for a large pool of public IP addresses by allowing many private IPs to use just one or a few public IPs.
- Security: NAT hides the private IP addresses of devices on the internal network from the public internet, adding a layer of protection.
- Flexibility: Devices on the private network can have their IP addresses changed without affecting connectivity to the internet or other networks.
A VPN passthrough solves the compatibility issue by allowing the encrypted VPN traffic to bypass the NAT process, ensuring that the VPN packets are delivered to their intended recipients without interference.
This enables seamless VPN connectivity while preserving the benefits of NAT for your local network.
Types of VPN Passthrough

VPN passthrough forwards your VPN traffic through the router, bypassing NAT in the process.
Instead of being blocked by NAT, we can use VPN passthrough functionality on the router.
VPN passthrough allows the router to identify and properly handle VPN protocols like PPTP, L2TP, and IPsec.
The specific implementation of VPN passthrough varies depending on the VPN protocol being used.
However, the general principle involves modifying the VPN data channels to include additional identifier fields, such as Call IDs or Session IDs.
The router then associates this data channel traffic with the corresponding control channel connection using these identifiers and the destination IP address, allowing it to correctly forward the VPN data packets to the server by translating the private IP/ports while leaving the encrypted payload untouched.
PPTP Passthrough
PPTP passthrough allows VPN traffic to traverse through the NAT router or firewall by modifying how the PPTP protocol functions:
- PPTP uses a TCP control channel (port 1723) for tunnel establishment/management, and a GRE data channel for the encrypted data packets.
- GRE lacks port numbers, conflicting with NAT’s need for port translation.
- Passthrough adds a Call ID field to the GRE header, acting as as a substitute for port numbers.
- When a PPTP client initiates a VPN connection, it sends a request over the TCP control channel on port 1723, which the router allows through standard NAT rules.
- The PPTP server responds with a unique Call ID inserted into the GRE data channel packets.
- The router inspects the GRE packets, associating them with the control channel using the Call ID and destination IP.
- The router translates the client’s private IP/port and forwards the GRE data to the VPN server, establishing the PPTP VPN tunnel.
IPsec Passthrough
IPsec passthrough works using NAT-Traversal (NAT-T) technology:
- IPsec secures IP communications by authenticating/encrypting data packets at the IP layer but conflicts with NAT as it embeds IP addresses within the data stream.
- NAT-T encapsulates IPsec packets inside UDP packets that NAT can handle.
- The IPsec client behind NAT initiates a connection to a server, sending an IKE (Internet Key Exchange) packet over UDP port 4500.
- The NAT router detects this UDP traffic and translates the client’s private IP/port to a public IP/port.
- The IPsec server responds with an IKE packet in UDP, which NAT routes back to the client.
- After IKE negotiation, IPsec data (ESP packets) is also encapsulated in UDP packets using port 4500.
- NAT translates the UDP/IP headers but leaves the IPsec payload untouched, allowing the VPN traffic to pass through the router.
LT2P Passthrough
L2TP passthrough works similarly to PPTP, as L2TP originated from PPTP and L2F:
- Like PPTP, L2TP uses a TCP control channel (port 1701) for tunnel management, and a UDP data channel for encrypted packets.
- The UDP data channel lacks port numbers, conflicting with NAT’s translation requirements.
- L2TP passthrough adds a Session ID field to the L2TP over UDP header. This Session ID acts as a substitute for port numbers that NAT can use for translation.
- When an L2TP client initiates a VPN connection, it sends a request over the TCP control channel (port 1701). The router allows this traffic through using standard NAT rules.
- The L2TP server responds with a unique Session ID, which is inserted into the L2TP header of the UDP data channel packets.
- The router inspects the UDP packets and associates them with the corresponding TCP control channel connection based on the Session ID and destination IP address.
- The router then translates the private IP/port of the L2TP client to its public IP/port and forwards the UDP data packets to the VPN server, allowing the L2TP VPN tunnel to be established.
Is VPN Passthrough the Same as a VPN Client?
VPN passthrough and a VPN client are entirely different things. A VPN client is a software application installed on your device that allows you to configure your VPN’s connection settings. It’s through the VPN client that you choose your server, adjust your settings, and enable the connection.
VPN passthrough is a feature on your router that allows VPN clients to connect to the server using older protocols. It’s enabled in your router’s settings.
What’s the Difference Between VPN Passthrough and a VPN Router?
A VPN router is a router with VPN software installed on it. It encrypts traffic from all devices on your local network, protecting them simultaneously.
You can buy VPN routers pre-installed with VPN software or flash compatible router with custom firmware like OpenWrt or FreshTomato. VPN routers support modern VPN protocols like OpenVPN and WireGuard, offering advanced features.
The VPN router acts as the VPN client, establishing a tunnel between itself and the VPN server. This allows devices without native VPN support (e.g., game consoles, smart TVs, IoT) to connect securely.
In contrast, VPN passthrough is a feature on regular routers that allows VPN traffic to pass through by modifying the protocol headers for NAT compatibility. With passthrough, the VPN client runs on your device, not the router.