New Tunneling Protocol Vulnerabilities
Over 4 million internet hosts, including VPN servers and private home routers, are vulnerable to being hijacked to perform anonymous attacks and provide access to their private networks.
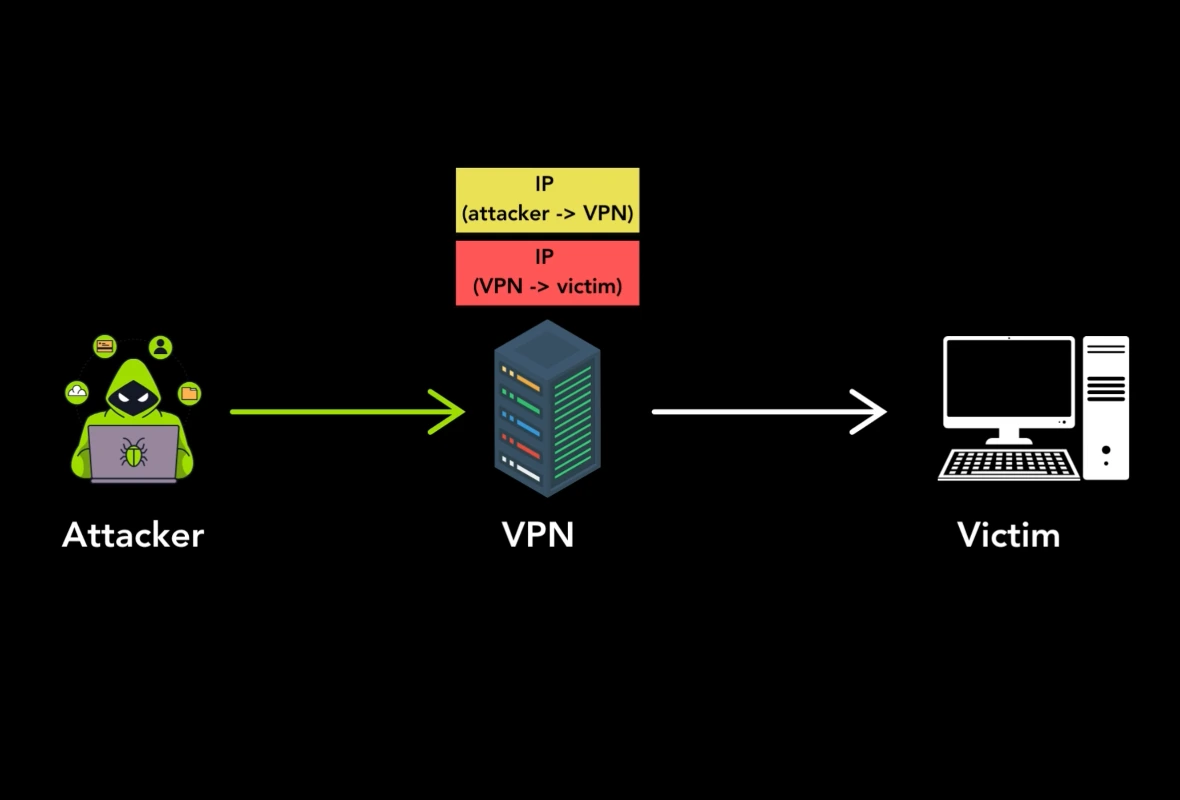
New vulnerabilities in multiple tunneling protocols allow attackers to hijack affected internet hosts to perform anonymous attacks and gain unauthorized network access.
A large-scale internet scan has identified 4.2 million open tunneling hosts, measuring the extent of these new vulnerabilities, along with that of a previously-known flaw in a related tunneling protocol, for the first time.
Top10VPN has again collaborated with leading security researcher Mathy Vanhoef to share this discovery ahead of its presentation at the USENIX 2025 conference in Seattle.
Vulnerability Details:
- Nature of vulnerability: Internet hosts that accept tunneling packets without verifying the sender’s identity can be hijacked to perform anonymous attacks and provide access to their networks.
- Affected tunneling protocols: IPIP/IP6IP6, GRE/GRE6, 4in6, 6in4.
- Total vulnerable hosts: 4.26 million hosts, including:
- VPN servers
- ISP home routers
- Core internet routers
- Mobile network gateways and nodes
- CDN nodes (incl. Meta and Tencent)
- Most affected countries: China, France, Japan, the U.S. and Brazil.
- Autonomous Systems (AS) affected: Over 11,000 worldwide. Most affected were Softbank, Eircom, Telmex, and China Mobile. Almost 40% of vulnerable ASs fail to filter spoofing hosts.
- Impact:
- Vulnerable hosts can be abused as one-way proxies, enabling a range of anonymous attacks.
- Many hosts also allow source IP spoofing to avoid detection.
- Potential access to private networks.
- Attacks include new DoS techniques and DNS spoofing, which in turn enables traditional DoS attacks, off-path TCP hijacking, SYN floods, and certain WiFi attacks.
- Identifiers:
- GRE, GRE6: CVE-2024-7595
- 4in6, 6in4: CVE-2025-23018/23019
- GUE: CVE-2024-7596 (no known affected hosts)
Security Impact of Open Tunneling Hosts
We worked with Professor Vanhoef to determine the prevalence and security impact of open tunneling hosts on the internet.
As shown in the video walkthrough below, these hosts accept unauthenticated tunneling traffic from any source. This means they can be abused as one-way proxies to perform a range of anonymous attacks.
Vulnerable hosts can also potentially be abused to gain access to victims’ private networks.

Watch Prof Vanhoef explain the security impact of open tunneling hosts
Prof. Vanhoef worked with CERT/CC to better inform affected parties in order to secure as many vulnerable hosts as possible.
Our goal in publishing this research is to inform the public of the alarmingly widespread nature of this family of vulnerabilities, particularly as it can affect home routers and VPN servers.
We also hope to educate people on how to configure internet-exposed devices to use tunneling protocols more securely and stay safe against the threats illustrated in this report.
Tunneling protocols are an essential backbone to the internet. They link disconnected networks and are commonly used in VPN solutions to encapsulate traffic.
A limitation of pure tunneling protocols like IPIP and GRE is that they don’t authenticate or encrypt traffic. To secure these protocols, they must be combined with IPsec.
Unfortunately, tunneling protocols are often used without additional security. This allows an attacker to inject malicious traffic into a tunnel.
Cybersecurity researcher Livneh Yannay previously discovered that IPv4 hosts accepted unauthenticated IPIP traffic from any source (CVE-2020-10136).[1]
As a result, an attacker can send an IPIP packet to a vulnerable host, which will strip the outer header and forward the inner IP packet without authenticating the sender.
That initial discovery prompted several key questions that formed the basis for this subsequent research:
- Are IPv6 hosts vulnerable?
- Are other tunneling protocols vulnerable?
- How to scan for vulnerable hosts?
- What are the security implications of vulnerable tunneling hosts?
- What are the practical defenses?
Further Reading:
- Download the full paper by Angelos Beitis and Mathy Vanhoef, Haunted by Legacy: Discovering and Exploiting Vulnerable Tunneling Hosts.
- Our previous reports on security flaws: SSID Confusion and WiFi authentication vulnerabilities.
Vulnerable Tunneling Protocols
To answer the questions above, Prof. Vanhoef and Beitis developed a series of probes to scan the entire IPv4 address space of the internet (3.7 billion IPs) and 10 million IPv6 addresses.
The scanning methods used were a combination of:
- Standard tunnel
- Subnet-spoofing
- Spoofing
- 6to4 & IPv4-mapped address
- Tunneled ICMP Echo/Reply
- Tunneled ICMP TTL Expired
Refer to the full paper for more detail on scanning methodology.
Vulnerable Host Scan Results
The following table summarizes the results of the scans. It shows the total number of vulnerable hosts by protocol, along with the number of spoofing-capable hosts as a subset of that.
| Tunneling Protocol | Vulnerable Hosts | Spoofing Capable |
|---|---|---|
| IPIP | 530,100 | 66,288 |
| IP6IP6 | 217,641 | 333 |
| GRE | 1,548,251 | 219,213 |
| GRE6 | 1,806 | 360 |
| 4in6 | 130,217 | 4,113 |
| 6in4 | 2,126,018 | 1,650,846 |
Deduping the above figures to account for hosts that were vulnerable on multiple protocols gives us the following:
- Total vulnerable hosts: 4,262,893
- Spoofing-capable vulnerable hosts: 1,858,892
Note that it’s not a simple 1:1 ratio between vulnerable hosts and physical devices.
This is because a host is an allocated IPv4 or IPv6 address. A single physical machine might represent multiple hosts if it has multiple (virtual) network cards.
The Impact of Spoofing-Capable Hosts
All vulnerable hosts can be hijacked to perform anonymous attacks, as the outer packet headers containing an attacker’s real IP address are stripped. These attacks are easily traceable to the compromised host, however, which can then be secured.
Spoofing-capable hosts can have ANY IP address as the source address in the inner packet, so not only does an attacker remain anonymous, but the compromised host also becomes much harder to discover and secure.
IPIP & IP6IP6
Total affected hosts: 747,741
What is the IPIP protocol? IPIP and its IPv6 counterpart IP6IP6 are tunneling protocols commonly used in Linux-based routing and network virtualization solutions to connect networks or subnets.
IPIP is also often used to encapsulate encrypted IPsec traffic between VPN endpoints. Cloud-based VPNs frequently use IPIP create tunnels between the user’s network and the cloud infrastructure.
OpenVPN can use IPIP tunneling in addition to its own encryption to provide an extra layer of abstraction and flexibility.
IPIP/IP6IP6 have no authentication or encryption and do not add any additional headers when transporting an inner packet.
Most common open ports in vulnerable hosts:
- HTTP
- HTTPS
Most affected domains:
fbcdnmyqcloudaiwan4399
The number of open HTTP and HTTPS ports suggests that IPIP/IP6IP6 vulnerable hosts were mainly servers.
This is supported by the prevalence of the fbcdn domain, which is Facebook’s content delivery network (CDN). The other top domains listed relate to Tencent’s cloud services.
There were also vulnerable VPN servers among the IPIP hosts.
GRE & GRE6
Total affected hosts: 1,550,557
What is the GRE protocol? Unlike IPIP, GRE (Generic Routing Encapsulation) adds a custom header before encapsulating the inner packet. This makes it more versatile, as it can encapsulate multiple protocols (not just IP).
It’s widely used in enterprise networks, and Cisco devices in particular. It can be used in the same way as IPIP with IPsec traffic, OpenVPN, and cloud-based VPNs.
GRE does have an optional key field but it offers little security, as it’s not encrypted and can be trivially eavesdropped.
Most common open ports in vulnerable hosts:
- BGP
- GTP-C
- GTP-U
Most affected domains:
telenetwindstream163data
GPRS Tunneling Protocol User Plane (GTP-U) and GPRS Tunneling Protocol Control (GTP-C) are used for data transfer in mobile networks, while BGP is the routing protocol for the internet.
This indicates the vulnerable GRE/GRE6 hosts were mainly core internet routers, specifically a mix of BGP routers and mobile network infrastructure, such as gateways and nodes.
It’s certainly quite alarming to consider there were over 1.5 million vulnerable hosts of this type, or 36% of the total.
In terms of the most-affected domains, Telenet is a Belgian ISP, Windstream is a U.S. internet provider, while 163data appears to be associated with China Telecom.
6in4 & 4in6
Total affected hosts: 2,256,235
What are 6in4 & 4in6? They are IPv6 tunneling protocols used to enable IPv6 traffic to traverse IPv4 networks, and vice versa.
6in4 (IPv6-in-IPv4) encapsulates IPv6 packets within IPv4 packets, allowing IPv6 networks to be connected over an IPv4 infrastructure.
4in6 (IPv4-in-IPv6) does the reverse, encapsulating IPv4 packets within IPv6 packets. This allows IPv4 traffic to be carried over an IPv6 network.
Almost half of all vulnerable hosts used the 6in4 and 4in6 protocols.
The notoriously slow adoption of IPv6 has arguably been a driver of how widespread this vulnerability appears to be.[2]
There would be much less need for the 6in4 and 4in6 protocols had the switch to IPv6 been more successful by now.
Most common open ports in vulnerable hosts:
- NTP
- SNMP
Most affected domains:
proxad49-tataidcbbtec
Open NTP (Network Time Protocol) and SNMP (Server Network Management Protocol) ports suggest that vulnerable 6in4 and 4in6 hosts are mostly routers provided by ISPs.
This is supported by the domains listed: proxadrelates to French ISP Free, 49-tata-idc is a Tata Teleservices (India) domain, and bbtec is associated with Japanese ISP Softbank.
For more detail, jump ahead to the section on vulnerable home routers.
Affected Devices
We can confidently infer the likely type of vulnerable devices discovered based on protocol, port number and domain information, where it’s available.
VPN Servers
Vulnerable VPN servers included:
- Consumer VPNs.
- Routers using Dynamic DNS for remote access, such as Synology devices.
- Business and local government VPNs
There were at least 1,365 likely VPN servers among the vulnerable hosts identified by the scans. This was calculated by filtering hosts’ domain names for text strings such as “VPN” and “Synology”.
For context, only around 125,000 hosts had domain names associated with them.
It’s almost certain therefore that the total number of vulnerable VPN servers is actually much higher than this.
In reality, there could be as many as 46,000 vulnerable VPN servers, if we make an estimate based on the ratio above.
Consumer VPNs
At least 130 of those 1,365 vulnerable VPN servers appeared to be associated with consumer VPN services.
Some vulnerable hosts appeared to be web servers for VPN website content. Other look to have been VPN endpoints or for other back-end services.
There were 17 vulnerable servers associated with Singapore-based VPN service AoxVPN, which has over a million active Android installations.[3] The VPN is also available on iOS, Windows and macOS and appears to be mainly targeted to Chinese- and English-speaking users.
Several domains relating to AoxVPN were associated with vulnerable hosts, including;
- The
aoxvpn.comdomain, which hosts their website. aoxvpnas a subdomain ofbplslb.com.avpn.coalso appears as a subdomain ofbplslb.com, confirming it to also be related to AoxVPN.
These hosts accepted IPIP packets from any source and so could be abused to perform the attacks outlined in this study.
While AoxVPN is an active service, the scans also detected vulnerable infrastructure for apparently-defunct VPN services whose servers were still online.
The host associated with the domain www.airfalconvpn.com was vulnerable and accepted unauthenticated tunneling traffic. This was the website of Indonesian VPN service AirFalcon VPN, which was active between 2022 and early 2024.
Elsewhere, another VPN domain, down.amanvpn.net, was associated with a vulnerable tunneling host.
AmanVPN was a free Hong Kong-based VPN provider with apps on various operating systems. Its previous Apple Store URL now redirects to RadhshVPN, which is also operated by the same company, Linguyn Mtd Infotech Limited.[4]
This discovery indicates that the infrastructure used for AmanVPN likely contained vulnerable tunneling servers.
Dynamic DNS Routers
Around 1,200 vulnerable hosts appeared to be dynamic DNS routers.
Most of these could be identified as Synology routers, which provide remote access via built-in VPN Plus Server software. The specific configuration of these devices appears to leave the host vulnerable.
Synology routers can be configured to use Dynamic DNS to automatically update a fixed domain name with the latest public IP address of networks that have a dynamic rather than static IP.
There were 12 vulnerable vpnplus.to and synology.me hosts. These domains are provided by Synology for its Dynamic DNS service.
Cross-referencing the vulnerable hosts with Censys data makes it possible to query the subject dn field of the hosts’ TLS certificates. This resulted in 1,007 matches for “Synology”.
There were also other Dynamic DNS domains associated with the vulnerable hosts.
Notably, 39 FreeboxOS.fr hosts (likely Free ISP customers in France) contained “VPN” in their domain name, suggesting they hosted vulnerable home router VPN servers.
Other common Dynamic DNS domain services are listed in this table below with the number of VPN domains found for each one.
| Dynamic DNS Service | VPN Domains |
|---|---|
| freeboxos.fr | 39 |
| softether.net | 25 |
| vpnplus.to | 8 |
| synology.me | 4 |
| ddns.net | 3 |
Each instance of a VPN domain likely corresponds to a home router also acting as a VPN server that provides remote access to users’ home networks.
Company VPNs
Around 171 hosts were associated with VPN domains connected to businesses or organizations. These hosts were mainly vulnerable over the GRE protocol.
The breakdown of vulnerable hosts by tunneling protocol was as follows:
- GRE: 123
- 6in4: 37
- IPIP: 10
- 4in6: 1
IP geolocation data revealed the vulnerable VPN servers to be in 33 different countries. The top five most-affected countries were as follows:
| Country | Company VPN Hosts |
|---|---|
| United States | 39 |
| China | 31 |
| Hong Kong | 28 |
| Canada | 15 |
| France | 12 |
Three domains related to U.S. city government websites. These vulnerable company VPN servers have since been secured however.
Clearly any attacker exploiting vulnerabilities in such hosts could cause an outsize impact, whether by exfiltrating sensitive data or by taking critical server infrastructure offline.
ISP Home Routers
Over 17% of all vulnerable hosts (726,194) stemmed from a misconfiguration in French ISP Free’s home routers.
Routers with hostname *.fbxo.proxad.net accepted unauthenticated plaintext 6in4 tunneling packets traffic from any source.
This flaw allows attackers to abuse Free customers’ vulnerable home routers to spoof IPv6 source addresses and to perform DoS attacks.
There is also a risk an adversary could attack other devices within victims’ home networks.
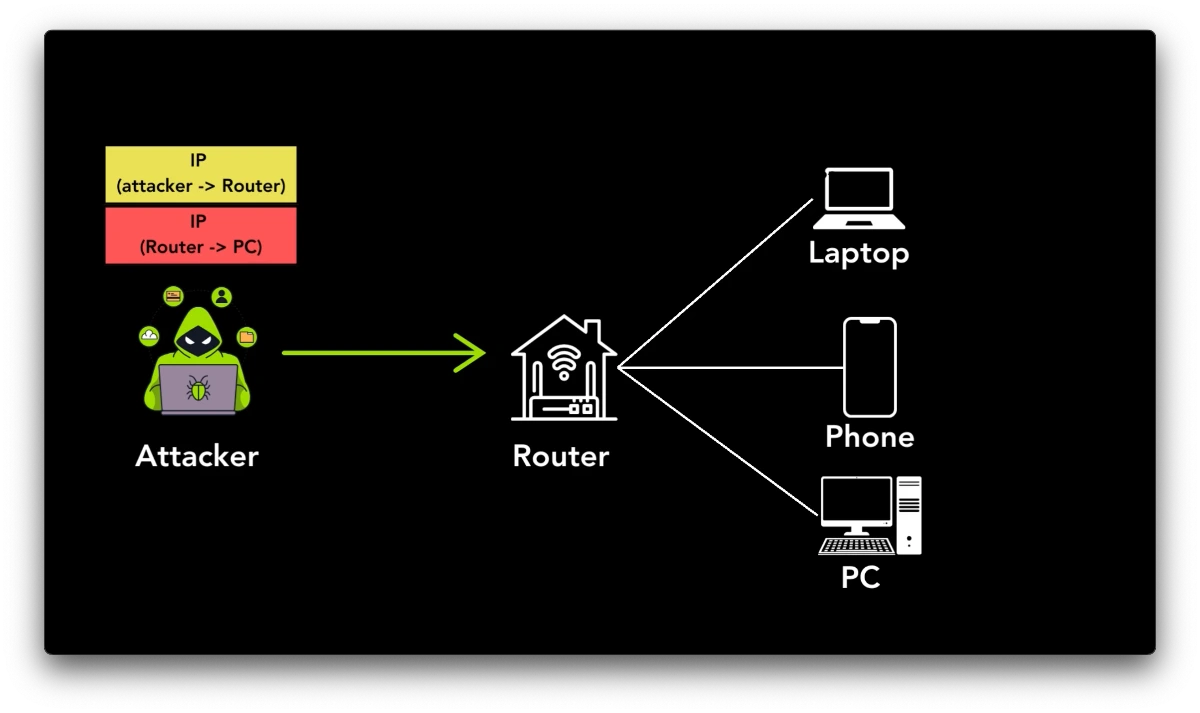
A home router that accepts unauthenticated tunneling packets could provide access to its network.
An attacker could use the compromised router to gain access to internal security cameras, data stored on insecure devices, or seize control over vulnerable home automation systems.
Ethical restrictions, however, meant that this could not be tested and verified in practice.
The responsible disclosure process with Free confirmed that the vulnerable hosts in question were home routers. It’s not as clear, however, whether other affected ISP’s hosts were core internet routers or private home devices.
Note that the French ISP secured its affected routers after being made aware of the vulnerability.
The following table shows the five ISPs with the most vulnerable hosts:
| ISP | Country | Vulnerable Hosts |
|---|---|---|
| Free | France | 726,194 |
| Softbank | Japan | 238,841 |
| Eircom Ltd | Ireland | 7,557 |
| Telmex | Colombia | 1,145 |
| Telmex | Chile | 470 |
Geolocation Analysis
Prof. Vanhoef’s scans detected vulnerable hosts in 218 of 249 territories around the world.
As this map shows, the Asia-Pacific region had the greatest concentration of vulnerable hosts, while Africa had the least.
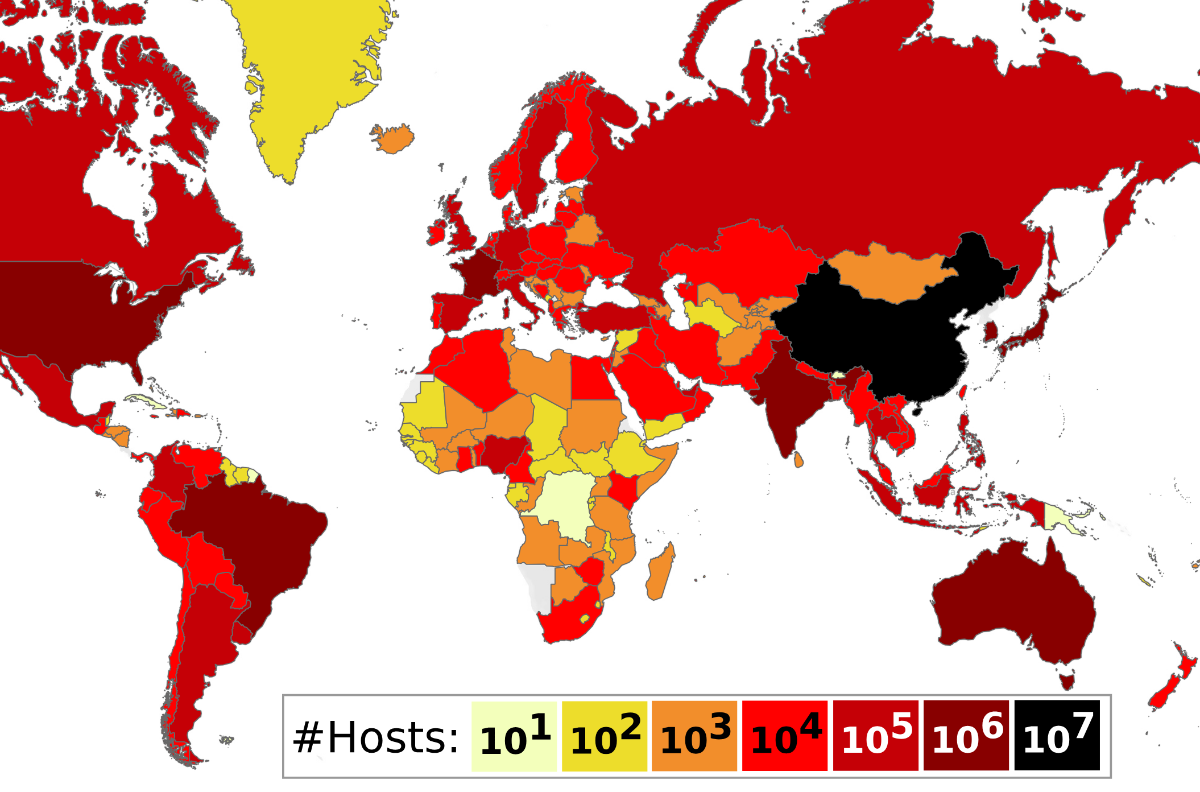
Map showing distribution of vulnerable tunneling hosts globally.
China and France had by far the most vulnerable hosts overall, and in significantly greater numbers than the countries with the next highest totals.
There were more spoofing-capable hosts in China than in all the other countries combined, or 59% of all such vulnerable hosts.
These hosts were greatly concentrated in a small number of Autonomous Systems (AS). Around 24% of spoofing-capable hosts were in a single AS.
This reveals the poor filtering practices employed by these particular ASs, which amplify the impact of the tunneling protocol vulnerabilities.
The greatest number of vulnerable IPv6 hosts were in France.
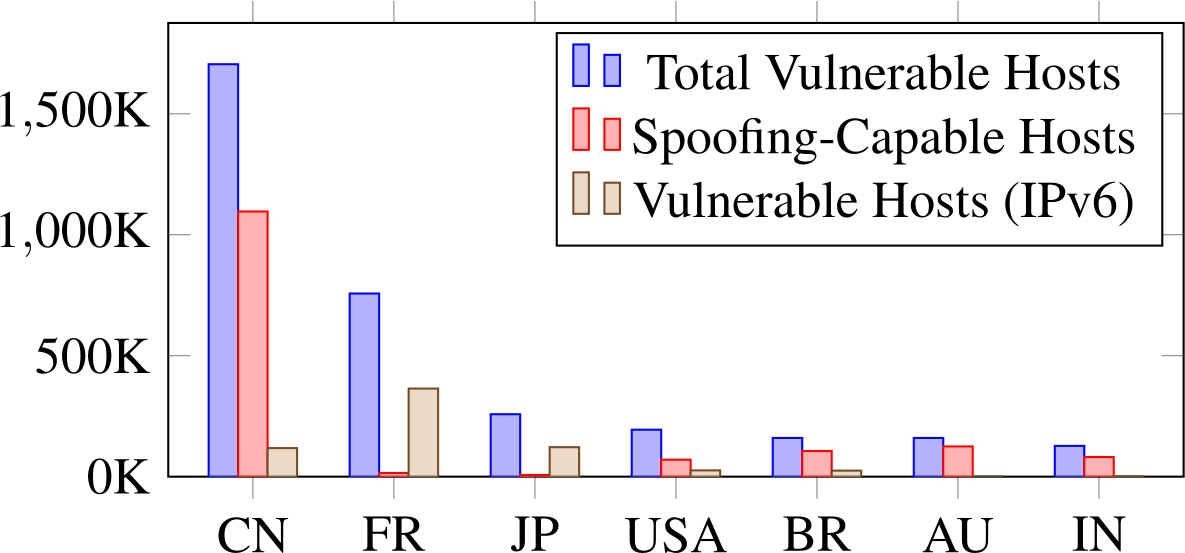
Chart showing countries with most open tunneling hosts.
While the countries in the chart above had the greatest absolute numbers of vulnerable hosts, this only represented a tiny percentage of all hosts in each country.
In China, for example, where the greatest number of hosts were located, this was only 0.52% of all Chinese hosts.
The countries with the greatest percentage of vulnerable hosts were as follows:
- Benin (2.78%)
- Zimbabwe (2.69%)
- Jamaica (1.45%)
- Laos (1.4%)
- Monaco (1.15%)
The chances of being affected by the vulnerabilities in this report were highest in these locations.
In terms of individual Autonomous Systems affected, there were 11,027 that were vulnerable in some degree, or around 1% of all ASs globally.
A handful of ASs were exceptionally vulnerable however. Two ASs accounted for 43% of all vulnerabilities while a single AS had 49% of all vulnerable IPv6 hosts.
It’s therefore likely that specific configurations or software used by these ASs were responsible for the vulnerabilities.
Attack Details
The lack of built-in authentication makes it trivial to inject traffic into the vulnerable protocols’ tunnels.
An attacker simply needs to send a packet encapsulated using one of the affected protocols with two IP headers.
The outer header contains the attacker’s source IP with the vulnerable host’s IP as the destination.
The inner header’s source IP is that of the vulnerable host IP rather than the attacker. The destination IP is that of the target of the anonymous attack.
When the vulnerable host receives this malicious packet, it automatically strips the outer IP header and forwards the inner packet to its destination.
As the source IP on this inner packet is that of the vulnerable but trusted host, it slips past any network filters.
This transmission of spoofed traffic renders the vulnerable host a one-way proxy.
If the vulnerable host is able to spoof IPs due to poor filtering on the part of its AS, then this allows the attacker to use any IP address as the source IP of the inner packet.
This prevents a backtrace to identify the source of an attack and secure it, which means that a spoofing-capable vulnerable host can potentially be abused indefinitely.
Prof. Vanhoef and Beitis discovered that it was possible to abuse a vulnerable host in new ways, outlined below.
Spoofing-capable hosts can also be abused to perform traditional attacks, such as DNS spoofing, traditional amplification DoS attacks, off-path TCP hijacking, SYN floods, certain WiFi attacks and so on.
1. Ping-pong Amplification Attack
This novel DoS attack loops packets between vulnerable hosts.
The packets are constructed to have as many recursively nested tunneling packets as possible until the maximum packet size is reached.
By looping these packets between hosts it amplifies the amount of bytes-per-second sent by the attacker.
The result is a DoS attack that can also be used to cause an Economic Denial of Sustainability (EDoS). This works by increasing the victim’s costs on the cloud as the data overload is outgoing rather than inbound.
2. Tunneled-Temporal Lensing (TuTL)
This new attack sends traffic over multiple chains of different vulnerable hosts to arrive simultaneously at the victim.
This peak of inbound traffic is called the pulsing window and causes benign traffic to be dropped.
3. Routing Loop DoS
This attack simply involves sending an IPv6 packet with ::IPV4_ADDRESS_IN_HEX as the destination.
This causes Linux to loop the packet on the tunneling interface until the hop limit field reaches zero.
In practice, this means the packet is sent and transmitted 256 times on the same interface.
4. Abusing Abuse Reports
Vulnerable hosts allow an adversary to spoof traffic that triggers abuse reports towards a victim.
This can lead to an administrative DoS attack, as receiving multiple abuse reports may cause the hosting provider to disable the victim’s account.
Impact on Victims
The impact on victims of these DoS attacks can include network congestion, service disruption as resources are consumed by the traffic overload, and crashing of overloaded network devices.
It also opens up opportunities for further exploitation, such as man-in-the-middle attacks and data interception.
For a full technical explanation of these attacks, see the full paper.
Defenses
There are two possible types of defense against these vulnerabilities: host and network.
Host Defenses
These defenses can be implemented at the host-level, ie on individual vulnerable internet-facing devices.
Summary of Host Defenses
- Only accept tunneling packets from trusted sources.
- Use more secure tunneling protocols.
While only accepting tunneling packets from trusted sources would in theory prevent attacks, spoofing such a source would sidestep this defense.
The only foolproof defense is to use a more secure set of protocols to provide authentication and encryption, i.e. IPsec or WireGuard
IPsec and WireGuard can be used to protect any of the vulnerable tunneling protocols. Hosts should therefore only accept tunneling packets protected by IPsec or WireGuard and drop all others.
Network Defenses
These defenses can be implemented by ISPs and other network owners on routers or other internet middleboxes to protect hosts on that network.
Summary of Network Defenses
- Implement traffic filtering on routers and middleboxes.
- Deep packet inspection (DPI) for malicious tunneling packets.
- Block all unencrypted tunneling packets.
Ingress and egress traffic filtering prevents an adversary from forcing a host to spoof packets.
DPI can be used to detect and drop recursively nested packets, for example. Similarly, those with inner packet TTL value 0, as such packets can be used to identify vulnerable hosts.
Where possible, networks could also block all ingoing and outgoing unencrypted tunneling packets.
Server Testing Code:
IT admins who want to test whether their own hosts/servers accept unauthenticated tunneling traffic can request access to the scanning scripts used in this research.
Visit the project’s Github for further details on how to do this, as the code is not yet publicly available to prevent abuse.
About Top10VPN Research
Mathy Vanhoef is a network security researcher whose major discoveries have included Dragonblood, KRACK Attack, TunnelCrack, and SSID Confusion.[5][6][7][8]
He is also a professor at the Department of Computer Science at KU Leuven, Belgium, where he is part of the DistriNet (Distributed Systems and Computer Networks) research group.
At Top10VPN, we only collaborate with carefully-vetted external researchers and ensure the relevant parts of our Responsible Disclosure Policy are followed at all times.
Vulnerabilities identified in this report have been reported to appropriate organizations and patched prior to publication.
The authors of all our investigations abide by the journalists’ code of conduct.
References
[1] https://mcfp.felk.cvut.cz/publicDatasets/pocorgtfo/contents/articles/21-03.pdf ↩
[2] https://blog.apnic.net/2024/10/22/the-ipv6-transition/ ↩
[3] https://play.google.com/store/apps/details?id=com.craftvpn.craft ↩
[4] https://apps.apple.com/it/app/vpn-amanvpn-vpn-proxy/id1575499950?l=en ↩
[5] https://www.zdnet.com/article/new-dragonblood-vulnerabilities-found-in-wifi-wpa3-standard/ ↩
[6] https://www.cloudflare.com/en-gb/learning/security/what-is-a-krack-attack/ ↩
[7] https://www.theregister.com/2023/08/10/tunnelcrack_vpn/ ↩
[8] https://www.darkreading.com/endpoint-security/flaw-in-wi-fi-standard-can-enable-ssid-confusion-attacks ↩