What Is Browser Fingerprinting?
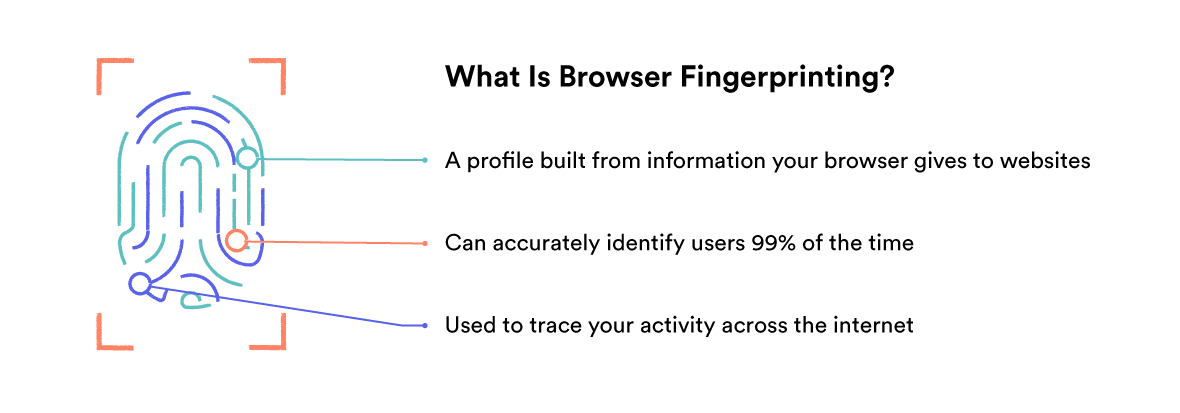
Browser fingerprinting works by collecting lots of information about your web browser, device, and software settings as you use the Internet. These attributes are then combined to create a “hash” which can be used to identify you.
Each individual datapoint might not reveal much by itself, but the combination of dozens of data points can create a fingerprint that’s entirely unique to you. That means it’s possible for websites, data brokers, advertisers, or law enforcement to identify you and profile your activities online.
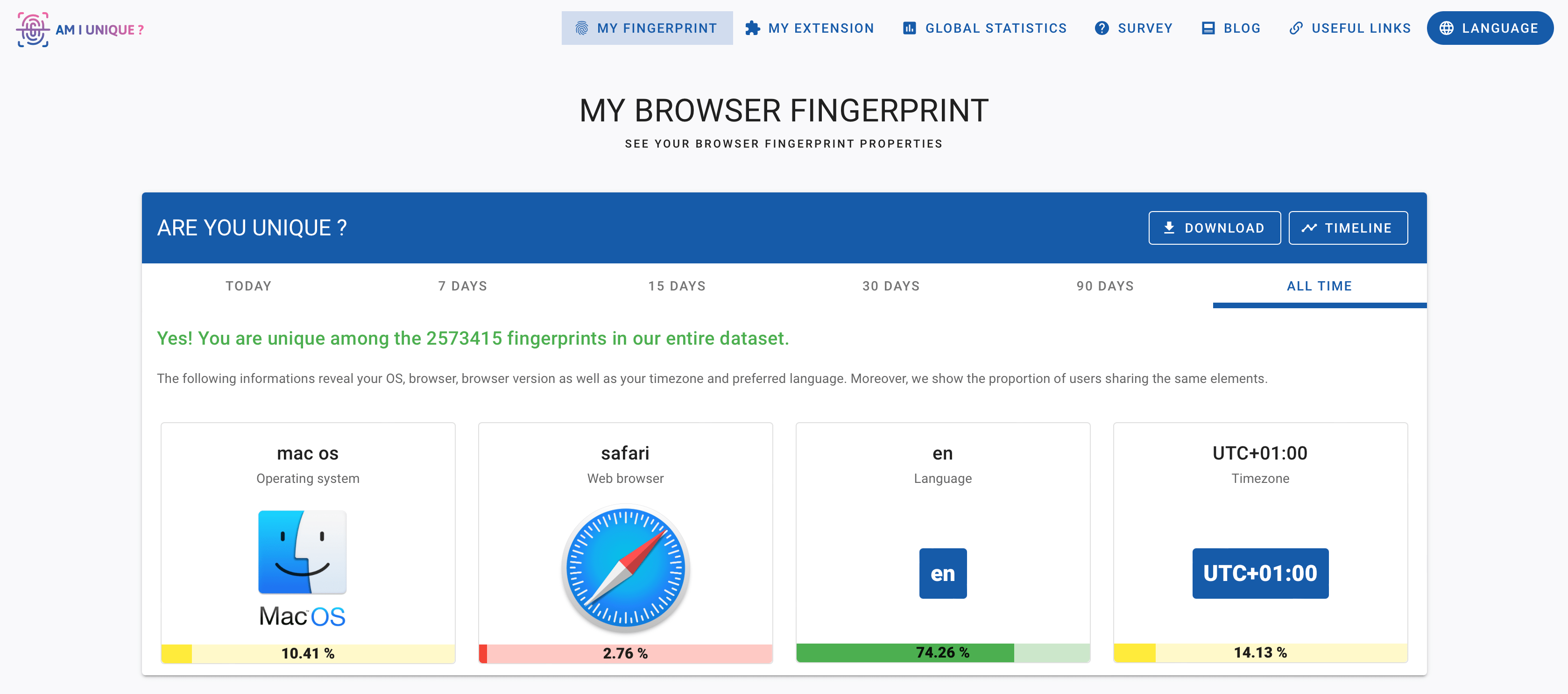
When browser fingerprinting was first developed in 2010, it identified between 83.6% and 94.2% of browsers uniquely. Similarly, research from 2020 found that between 67.6% and 93.1% of users could be tracked.
You’ve probably heard of cookies. They’re small files that a website can store on your device to recognize you when you return, or to track your activities across websites.
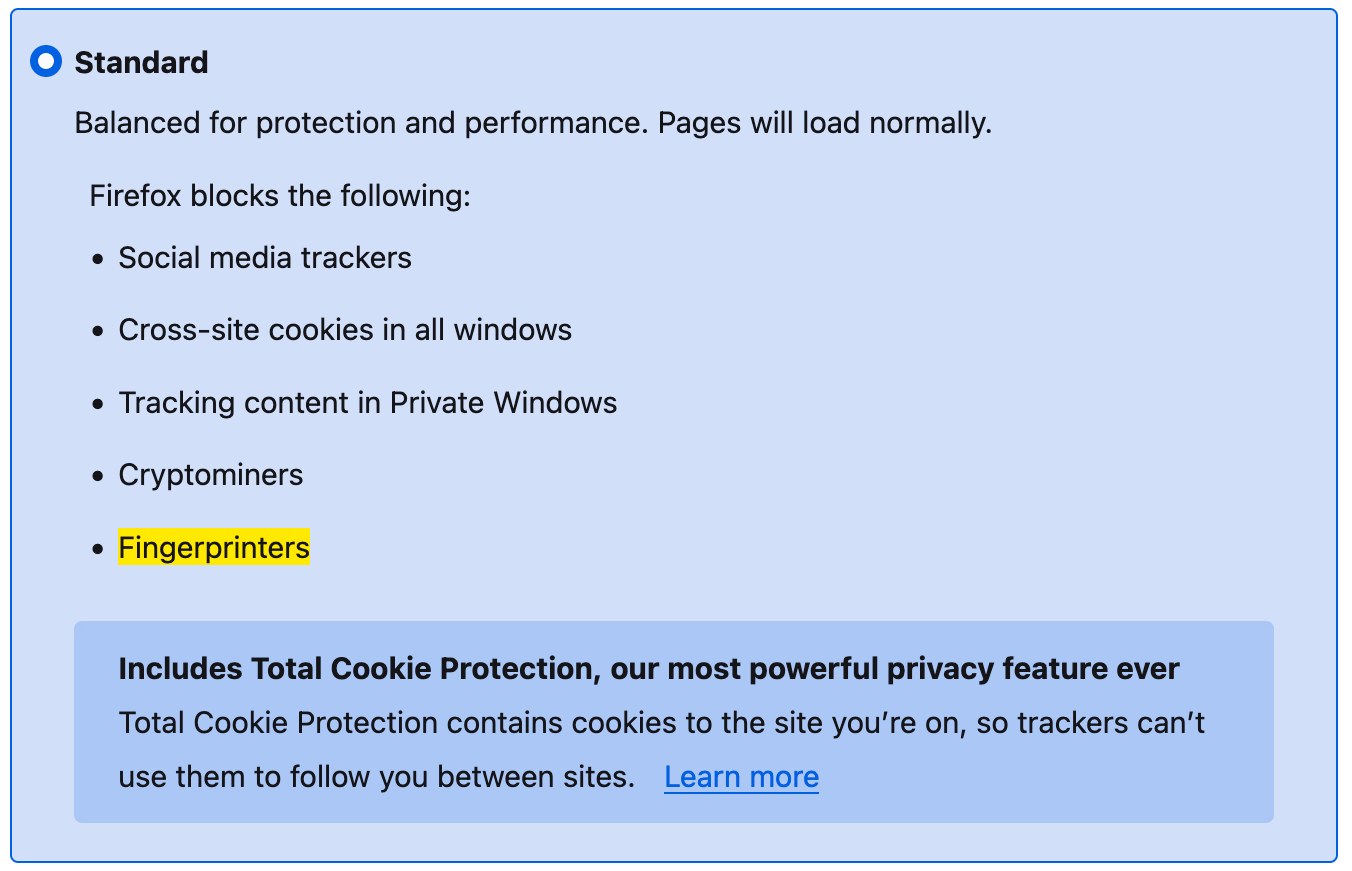
While most browsers have built-in features for blocking or removing cookies, browser fingerprinting is much harder to control. You can’t delete a browser fingerprint because it’s not stored on your computer.
However, browser fingerprints do change when the information they are based on changes. That means updating your browser or installing a new plug-in could change your fingerprint.
Browser fingerprints aren’t perfect for uniquely identifying someone, either. It is possible for different users to share a fingerprint, particularly on mobile devices where users are less likely to customize their settings.
Despite these limitations, browser fingerprints remain an effective way to identify and track web users.
Why Is Browser Fingerprinting Used?
The aim of browser fingerprinting is to better understand website visitors and to track them across visits, and even across websites. There are both positive and negative ways the technique can be used.
The positive uses of browser fingerprinting typically involve improving security:
- Adding authentication: A website can identify your usual browser and use it to simplify your login process. For example, if you use an unfamiliar device, a bank might challenge you with more security questions to make sure it’s really you.
- Detecting suspicious activity: A browser fingerprint can help to identify bots or fraudulent users. For example, it can identify one person who is trying to impersonate many, or can spot a small screen resolution that suggests someone is simulating multiple devices on a single monitor.
- Banning users: Fingerprinting can be used to ban users who break the rules on gambling sites. Fingerprinting can detect users who try to claim multiple registration bonuses, or who pretend to be several independent players in the same game.
The negative uses of browser fingerprinting include:
- Targeted advertising: An advertiser could use browser fingerprinting to build a profile of your interests based on the sites you visit. That information could be used to target ads at you, or it could be sold to other companies.
- Dynamic pricing: An online shop might charge more to customers who appear to be richer, for example by having more expensive devices or living in a wealthier area.
- Data harvesting: Browser fingerprinting enables data brokers and advertisers to collect information about web users even if they block cookies, use a VPN, or use private browsing mode. It’s unclear how this data is collected and traded, but the privacy and ethical risks are clear.